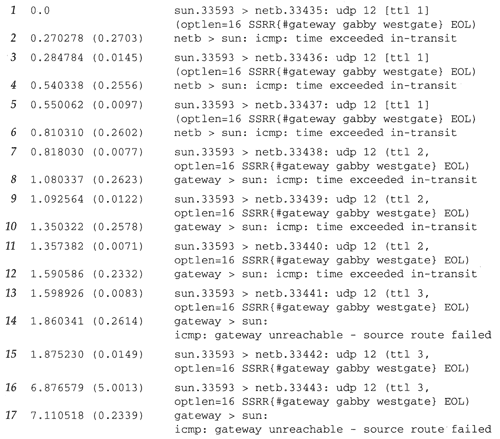
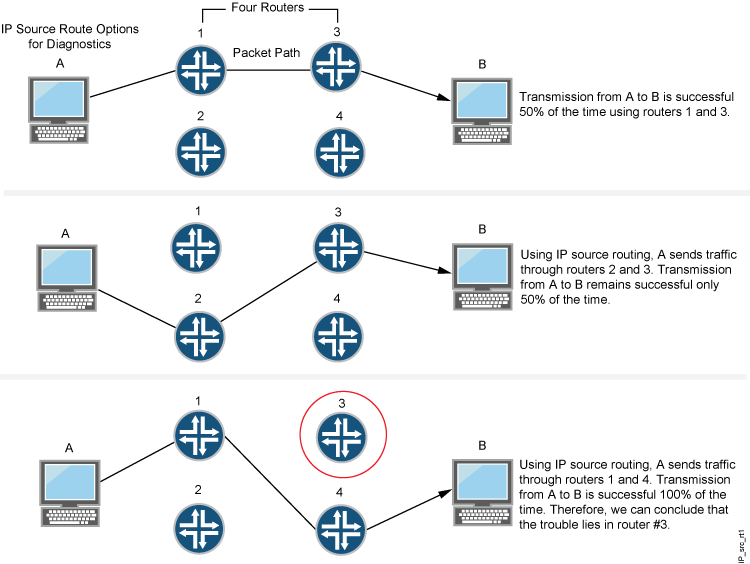
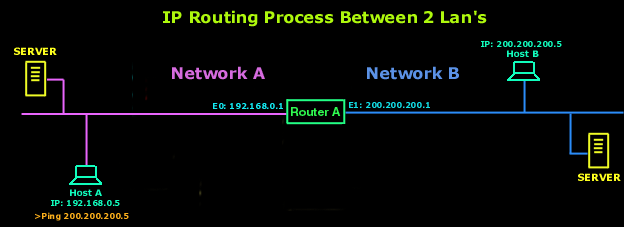
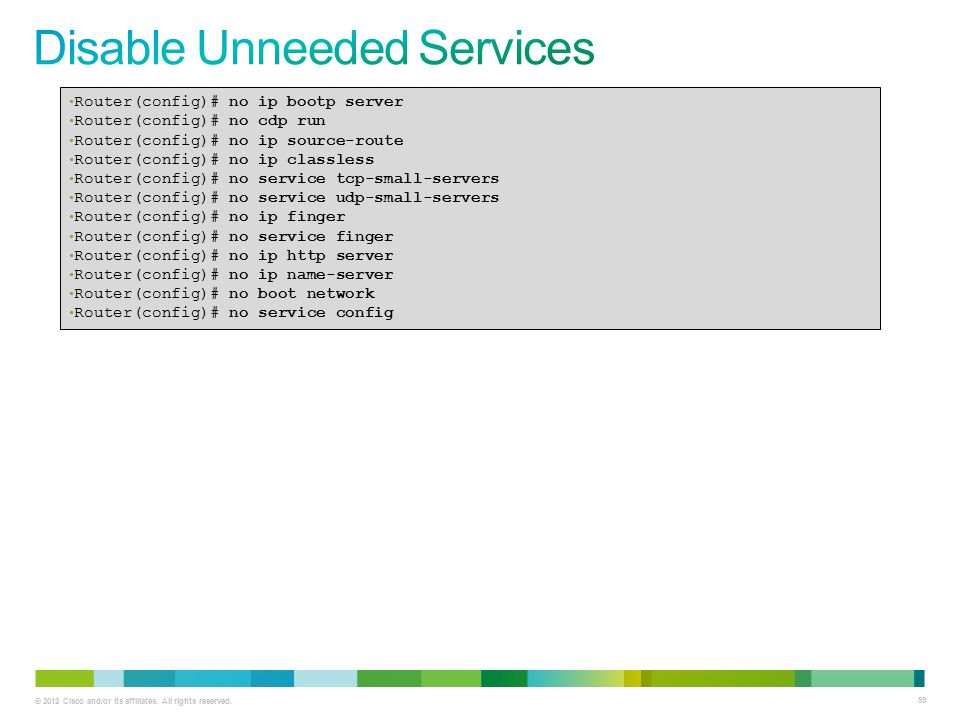
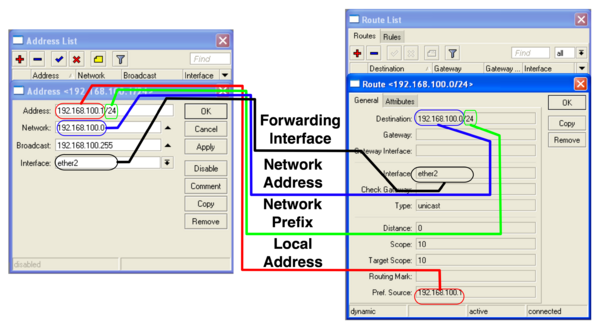
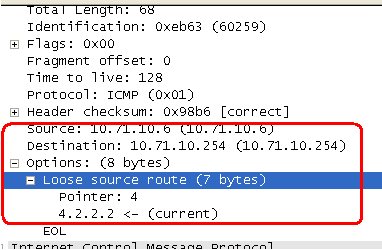
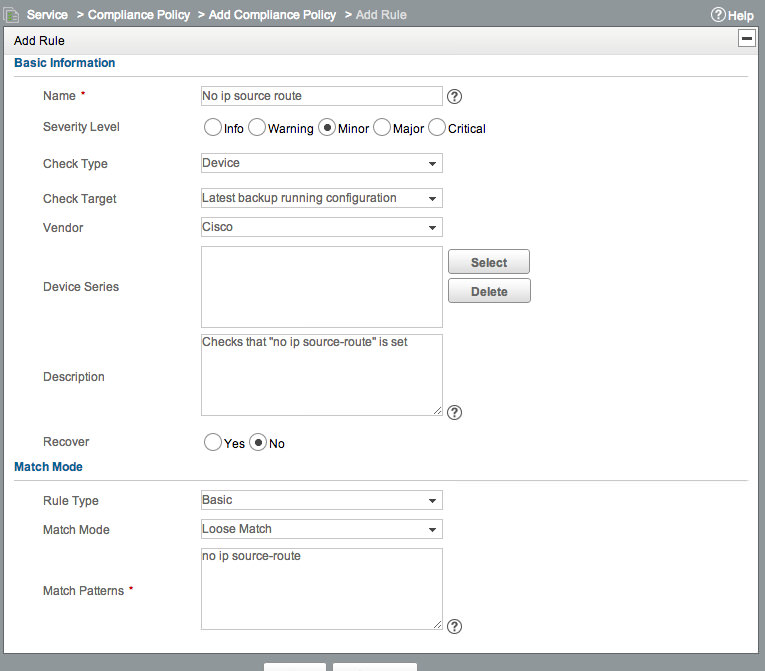
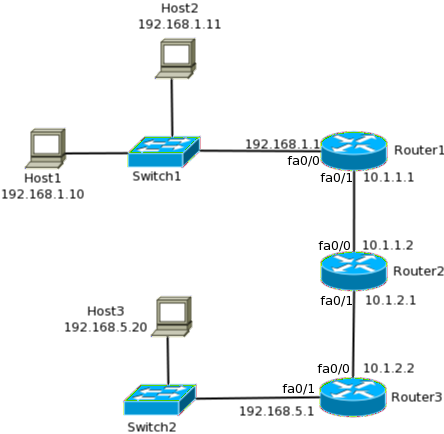
What type of routing (source/non-source) is supported in AD6LoWPAN? - Documents - AD6LoWPAN Reference Library - EngineerZone

8.5 IP Source Routing Option | TCP/IP Illustrated, Vol. 1: The Protocols (Addison-Wesley Professional Computing Series)